Plex Remote Access Through OPNsense VPN
TL;DR
This guide configures and tests Plex remote access on OPNsense by routing Plex traffic to WAN while keeping everything else on VPN.
Prerequisites:
- OPNsense with VPN routing
- Plex with static IP
- SSH access
What you’ll do:
- Create firewall aliases and rules for Plex bypass
- Configure port forwarding for external access
- Run eight tests to verify no VPN leakage
Running Plex when all traffic routes through VPN breaks remote access because most VPN providers don’t support port forwarding. This guide shows how to selectively route only Plex traffic to WAN.
Trade-off: Your ISP can see Plex traffic. Everything else stays encrypted through VPN.
Introduction
Plex remote access doesn’t work through VPN because Plex servers need to connect directly to plex.tv for authentication and relay services. This guide configures policy-based routing to send Plex traffic directly to WAN while everything else stays encrypted through VPN. Includes port forwarding for direct connections and verification tests.
Configuration Steps
Backup OPNsense config before making changes: System → Configuration → Backups
Step 1: Create Plex Aliases
Navigate to Firewall → Aliases and create the following:
Host Alias for Plex Server:
| Field | Value |
|---|---|
| Name | PLEX |
| Type | Host(s) |
| Content | 10.0.10.200 |
| Description | Plex Media Server IP |
Port Alias for Plex Ports:
| Field | Value |
|---|---|
| Name | PLEX_PORTS |
| Type | Port(s) |
| Content | 443, 1900, 3005, 8324, 32400, 32469, 32410:32414 |
| Description | Plex required ports |
Why these ports?
- 32400: Primary Plex server port (HTTPS)
- 443: Plex web interface and secure connections
- 1900: DLNA/UPnP discovery
- 3005: Plex Companion
- 8324: Roku via Plex Companion
- 32469: Plex DLNA Server
- 32410-32414: GDM network discovery
These aliases work the same way as the aliases created in the main OPNsense guide.
Step 2: Create WAN Port Forward Rule
Navigate to Firewall → NAT → Port Forward and create:
| Field | Value |
|---|---|
| Interface | WAN |
| Protocol | TCP |
| Source | Any |
| Destination | WAN address |
| Destination Port Range | 32400 |
| Redirect Target IP | PLEX (alias) |
| Redirect Target Port | 32400 |
| NAT reflection | Disable |
| Filter rule association | Pass |
| Description | Redirect WAN to PLEX on 32400 |
Why disable NAT reflection? NAT reflection allows internal devices to access Plex using your public WAN IP, which adds unnecessary complexity and can cause routing issues. Internal devices should always use the local IP (10.0.10.200) directly.
Step 3: Create Floating Rules for Plex Bypass
Navigate to Firewall → Rules → Floating and create the following rule:
Plex Bypass VPN to WAN:
Note: Select the specific interface where your Plex server resides. This floating rule applies only to that interface.
| Field | Value |
|---|---|
| Action | Pass |
| Quick | ✓ Check |
| Interface | Your Plex VLAN (e.g., DMZ_VL10) |
| Direction | in |
| Protocol | TCP/UDP |
| Source | PLEX (alias) |
| Destination | !IPv4_RFC1918 (inverted - external traffic only) |
| Destination Port | PLEX_PORTS (alias) |
| Gateway | WAN_DHCP |
| Description | PLEX bypass VPN to WAN |
| Log | ✓ Enable (for troubleshooting) |
Critical: Rule Placement
This rule MUST be placed ABOVE your VPN routing rules in the floating rules list. Firewall rules are processed top to bottom, and the first match wins (with quick enabled).
Correct rule order:
Priority | Rule Description
----------|--------------------------------------------------
1 | Anti-lockout (allow ports 443, 22 to firewall)
2 | Allow VPN tunnel establishment (MULLVAD_ENDPOINTS to WAN)
3 | PLEX bypass VPN to WAN ← HERE
4 | VPN routing for VPN_OUT_IG (route to WAN_VPN_GRP)
5 | Kill switch (block all other WAN traffic)Why order matters:
Rules with quick enabled stop processing on first match. If you followed the main guide, your floating rules already include anti-lockout, VPN establishment (MULLVAD_ENDPOINTS), and VPN routing (VPN_OUT_IG). Plex bypass goes between VPN establishment and VPN routing.
Step 4: Verify Configuration
After applying changes, verify your configuration:
Check aliases exist:
# SSH into OPNsense
pfctl -t PLEX -T show
# Should output: 10.0.10.200 ← Plex IP Check port forward exists:
pfctl -sn | grep "rdr.*32400.*PLEX"
# Should show a redirect rule on WAN interface like this:
rdr on igb0 inet proto tcp from any to (igb0) port = 32400 -> <PLEX> port 32400 round-robinCheck floating rules loaded:
pfctl -sr | grep "from <PLEX>" | grep "route-to"
# Should show bypass rules routing to WAN gatewayTesting Your Setup
Now that configuration is complete, verify everything works correctly.
Test 1: Verify Policy-Based Routing Rules Are Loaded
What we’re testing: Firewall rules route Plex traffic to WAN gateway
From: OPNsense SSH
How to test:
pfctl -sr | grep "from <PLEX>" | grep "route-to"Expected output:
12+ lines showing bypass rules for various Plex ports routing to WAN gateway via your WAN interface.
pass in log quick on vlan0.10 route-to (igb0 192.168.1.1) inet proto tcp from <PLEX> to ! <IPv4_RFC1918> port = https flags S/SA keep state
pass in log quick on vlan0.10 route-to (igb0 192.168.1.1) inet proto tcp from <PLEX> to ! <IPv4_RFC1918> port = 32400 flags S/SA keep state
pass in log quick on vlan0.10 route-to (igb0 192.168.1.1) inet proto tcp from <PLEX> to ! <IPv4_RFC1918> port = 3005 flags S/SA keep stateIf this fails:
- Empty output means floating rules are not loaded or misconfigured
- Check rule order in
Firewall → Rules → Floating - Verify Plex bypass rule is above VPN routing rules
- Ensure
quickis enabled on the Plex bypass rule
Test 2: Verify Active Connections Use WAN
What we’re testing: Live Plex connections show WAN IP, not VPN IP
From: OPNsense SSH (while Plex is actively streaming or connecting)
How to test:
# Replace PLEX_IP and WAN_IP with your actual IPs
pfctl -ss | grep "10.0.10.200" | grep "YOUR_WAN_IP"Expected output:
Multiple connection states showing WAN IP as the translated source address:
# Example showing Plex using WAN IP (203.0.113.45) not VPN IP
all tcp WAN_IP:30372 (10.0.10.200:50388) -> 247.182.154.46:443 ESTABLISHED:ESTABLISHED
all tcp WAN_IP:13968 (10.0.10.200:43042) -> 176.236.103.219:443 ESTABLISHED:ESTABLISHED
all tcp WAN_IP:60469 (10.0.10.200:41116) -> 76.144.224.23:443 ESTABLISHED:FIN_WAIT_2The format is: WAN_IP:port (PLEX_IP:port) -> destination:port
Example breakdown:
203.0.113.45:30372 (10.0.10.200:50388) -> 247.182.154.46:443
└─────┬─────┘ └──────┬──────┘ └───────┬────────┘
Your WAN IP Plex local IP Remote Plex client
(NAT translated) (actual source) (destination)If this fails:
- No results: Plex isn’t actively connecting, or rules aren’t working
- Shows VPN IP instead: Plex traffic is going through VPN (rule order issue)
- Verify Plex is actively streaming or accessing plex.tv
- Check that connections exist:
pfctl -ss | grep "PLEX_IP"
Test 3: Verify No Plex Traffic Through VPN
What we’re testing: No Plex traffic leaking through VPN tunnels
From: OPNsense SSH
How to test:
# Check for any connections from Plex going through wg interfaces
# Replace PLEX_IP and VPN interface names with your actual values
# Common VPN interface names: wg0, wg1, UK_VPN, DE_VPN
pfctl -ss | grep "10.0.10.200" | grep -E "wg0|wg1|UK_VPN|DE_VPN" | wc -lExpected output:
0A count of 1 may indicate a single stale connection established before rules were applied. This is normal and will timeout naturally.
If this fails:
- Count greater than 1 or increasing over time indicates active VPN leakage
- Plex traffic is going through VPN instead of WAN
- Check rule order (Plex rules must be before VPN rules)
- Verify gateway on Plex floating rule is set to WAN_DHCP
Test 4: Verify Port Forward Exists
What we’re testing: Port 32400 forwards from WAN to Plex server
From: OPNsense SSH
How to test:
pfctl -sn | grep "32400.*<PLEX>"Expected output:
One or more redirect rules showing port 32400 forwarding to Plex server. The critical rule is on your WAN interface.
rdr on igb0 inet proto tcp from any to (igb0) port = 32400 -> <PLEX> port 32400 round-robinNote: You may see multiple rdr rules for different interfaces (VLANs, VPN interfaces, etc.). This is normal - the important one is the rule on your WAN interface (igb0 or whatever yours is).
If this fails:
- No output means port forwarding is not configured on WAN interface
- Navigate to
Firewall → NAT → Port Forward - Verify rule exists with Interface = WAN
- Check that rule is enabled (not disabled or deleted)
Test 5: Test External Plex Access from Internet
What we’re testing: Plex is accessible from outside your network
From: Device OUTSIDE your network (mobile data, remote VPS, friend’s house)
How to test:
# Replace WAN_IP with your actual WAN IP
curl -I http://WAN_IP:32400/web/index.html --max-time 5Expected output:
HTTP 200 response with Plex-specific headers:
HTTP/1.1 200 OK
X-Plex-Protocol: 1.0
Cache-Control: no-cache
Accept-Ranges: bytes
Connection: Keep-Alive
Content-Type: text/htmlIf this fails:
Connection timeout:
- Firewall blocking inbound traffic (check WAN rules)
- ISP blocking port 32400 (try port 443 instead)
- Port forward not working (verify Test 4 passed)
Connection refused:
- Plex service not running on server
- Plex not listening on port 32400 (check Plex settings)
- Port forward misconfigured (wrong target IP)
Testing from inside your network won’t work due to routing and firewall rules - you must test from an external connection.
Test 6: Plex Self-Reported IP
What we’re testing: Plex correctly detects your public WAN IP, not VPN IP
From: Browser on any device
How to test:
- Access Plex web interface:
http://10.0.10.200:32400/web - Navigate to:
Settings → Network → Show Advanced - Check the “Public IP address” field
- Check the “Remote Access” status
Expected output:
- Public IP: Your WAN IP (NOT your VPN IP like 10.65.x.x)
- Remote Access: Green checkmark with “Fully accessible outside your network”
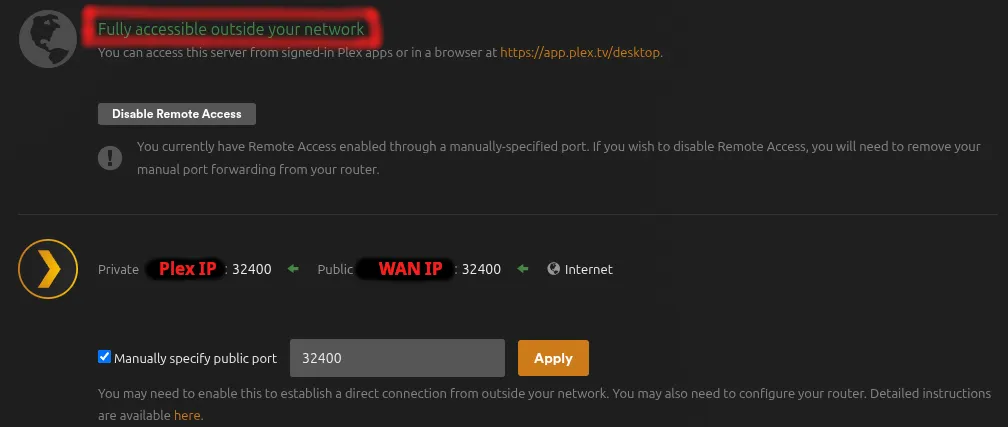
If this fails:
Public IP shows VPN IP:
- Plex traffic is going through VPN tunnel
- Rule order issue (Plex rules must be before VPN rules)
- Gateway not set to WAN_DHCP on floating rule
Remote Access shows “Not available outside your network”:
- Port forward not working
- WAN IP not accessible from internet
- ISP blocking port 32400
“Double NAT detected” warning:
- You’re behind carrier-grade NAT (CGNAT)
- ISP uses multiple layers of NAT
- Contact ISP or consider alternatives (VPS reverse proxy)
Test 7: DNS Resolution
What we’re testing: Plex can resolve external domains correctly
From: OPNsense SSH or Plex server
How to test:
drill @10.0.0.1 plex.tv AExpected output:
Valid IP addresses in AWS ranges (3.x.x.x, 34.x.x.x, 54.x.x.x):
;; ->>HEADER<<- opcode: QUERY, rcode: NOERROR, id: 34759
;; flags: qr rd ra ; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;; plex.tv. IN A
;; ANSWER SECTION:
plex.tv. 55 IN A 54.76.243.238
plex.tv. 55 IN A 34.254.54.72
plex.tv. 55 IN A 34.254.245.199
plex.tv. 55 IN A 3.248.163.211
;; Query time: 76 msec
;; SERVER: 10.0.0.1
;; WHEN: Thu Oct 2 13:27:06 2025
;; MSG SIZE rcvd: 89Note on plex.direct:
If using Mullvad or other filtering VPN DNS providers, drill @10.0.0.1 plex.direct A may return 0.0.0.0. This is expected behavior because some DNS filtering services block the plex.direct domain. This does not affect Plex functionality.
If this fails:
- No response, timeout, or SERVFAIL error indicates DNS issues
- Verify DNS server is operational:
configctl unbound status - Check Unbound is running:
service unbound status - Test with different DNS server:
drill @1.1.1.1 plex.tv A
Test 8: Verify Rule Processing Order
What we’re testing: Plex bypass rules are processed before VPN routing rules
From: OPNsense SSH
How to test:
# -n flag shows line numbers to verify rule order
pfctl -sr | grep -n "PLEX\|VPN_OUT_IG.*route-to" | head -20Expected output:
Plex bypass rules appear with lower line numbers than VPN routing rules:
103:pass in log quick on vlan0.10 route-to (igb0...) from <PLEX>...
104:pass in log quick on vlan0.10 route-to (igb0...) from <PLEX>...
105:pass in log quick on vlan0.10 route-to (igb0...) from <PLEX>...
...
185:pass in log quick on VPN_OUT_IG route-to (wg0...)...
186:pass in log quick on VPN_OUT_IG route-to (wg0...)...Why this matters:
Firewall rules are processed sequentially from top to bottom. With quick rules, the first match wins. Plex rules (lines 103-116 in example) must appear before VPN rules (line 185+) to catch Plex traffic before it can be routed through VPN.
If this fails:
- VPN rules have lower line numbers than Plex rules
- VPN rules will match first and route Plex through tunnel
- Navigate to
Firewall → Rules → Floating - Drag Plex bypass rules above VPN routing rules
- Apply changes and retest
Troubleshooting
Issue: Plex Shows VPN IP Instead of WAN IP
Symptoms:
- Plex Settings → Network shows VPN IP (10.65.x.x)
- Remote access unavailable
Solution:
- Check rule order:
pfctl -sr | grep -n "PLEX\|VPN_OUT_IG" | head -20 - Plex rules must have lower line numbers
- Navigate to
Firewall → Rules → Floating - Move Plex bypass rules above VPN routing rules
- Verify gateway is set to WAN_DHCP, not VPN gateway
Issue: Port 32400 Not Accessible Externally
Symptoms:
- External curl test times out
- Plex remote access shows “not available”
Solution:
Check port forward exists:
pfctl -sn | grep "32400"Check WAN firewall rules:
- Navigate to
Firewall → Rules → WAN - Verify rule exists allowing port 32400
- Should be auto-created by port forward
Check ISP blocking:
- Some ISPs block common server ports
- Try using port 443 instead (requires Plex config change)
- Test from mobile data connection
Check Plex is listening:
# From Plex server
netstat -an | grep 32400Issue: Plex Works Locally but Not Remotely
Symptoms:
- Local access to http://10.0.10.200:32400 works
- External access via WAN IP fails
Solution:
Verify you’re testing externally:
- Must test from device outside your network
- Use mobile data or remote VPS
- Internal testing won’t work due to routing
Check port forward NAT reflection:
- Navigate to
Firewall → NAT → Port Forward - Edit Plex port forward rule
- Verify “NAT reflection” is disabled
- Internal devices should use local IP
Verify WAN IP is correct:
curl ifconfig.meUse this IP for external access, not VPN IP
Issue: Plex Traffic Going Through VPN
Symptoms:
- Test 3 shows non-zero count (VPN leakage)
- Connections show VPN IP in pfctl -ss output
Solution:
Check floating rule gateway:
- Navigate to
Firewall → Rules → Floating - Edit Plex bypass rule
- Verify Gateway = WAN_DHCP (not WAN_VPN_GRP or VPN gateway)
Verify rule has “quick” enabled:
- Quick checkbox must be checked
- Without quick, rules continue processing
- Later VPN rules will match and override
Check source matches Plex alias:
pfctl -t PLEX -T showShould output your Plex server IP exactly
Issue: All Traffic Routing Through WAN
Symptoms:
- Non-Plex traffic shows WAN IP on whatismyip.com
- Kill switch not working
Solution:
Critical: Your VPN routing is broken
Check VPN tunnels are up:
wg showIf tunnels are down, revisit the VPN setup section from the main guide.
Both should show recent handshakes
Check gateway group:
- Navigate to
System → Gateways → Group - Verify WAN_VPN_GRP exists
- Contains both VPN gateways
Check VPN routing rules:
- Navigate to
Firewall → Rules → VPN_OUT_IG - Verify rule uses gateway WAN_VPN_GRP
- Rule should be enabled
Verify kill switch:
- Navigate to
Firewall → Rules → Floating - Kill switch rule should be last
- Blocks all WAN traffic except VPN_OUT_IG
Notes
Your ISP sees all Plex traffic with this configuration - connection times, data volumes, and remote IPs. Everything else (browsing, downloads, other services) remains encrypted through VPN. If this trade-off is unacceptable, use a VPN provider with port forwarding or run a VPS reverse proxy instead.
[references] ▸
- [1.1]Building a Secure Home Network with OPNsense — Complete firewall configuration with VPN and VLAN setup
- [1.2]Testing Your OPNsense Setup — General verification procedures for OPNsense
- [2.1]
- [2.2]
[changelog] ▸
- → Initial publication
Disclaimer
Use the information provided here at your own risk, but if you find errors or issues in this guide, leave a comment and I’ll try to address them ASAP.